Security is a journey, and adopting a Zero Trust approach is one of your best defenses against attackers. See how Veeam Data Platform can help you move closer to radical resilience and meet your compliance goals.
- Measure your adherence to best practices
- Implement strict authentication and authorization controls
- Detect, respond, and monitor for threats
-
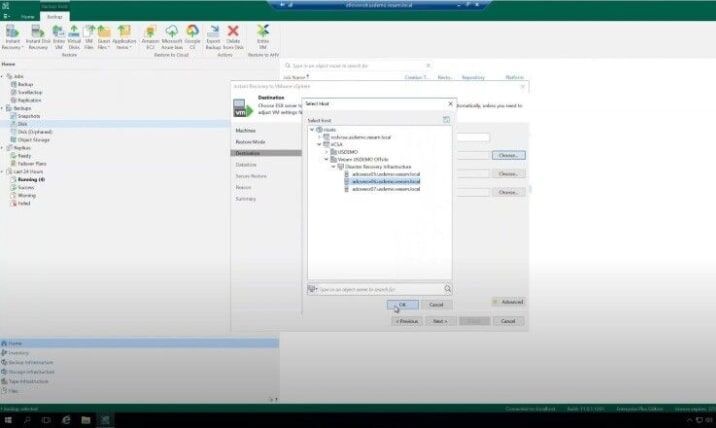
Demo #1
Four Security Tips to Keep Your Backups Safe
Attackers know that backups are your last line of defense and will do whatever they can to destroy them. Fortunately, Veeam provides the tools you need to ensure recoverability. Strengthen your security posture using tools such as the Security & Compliance Analyzer, Multifactor Authentication, and four‑eyes authorization while measuring your security score with the Veeam Threat Center.
-
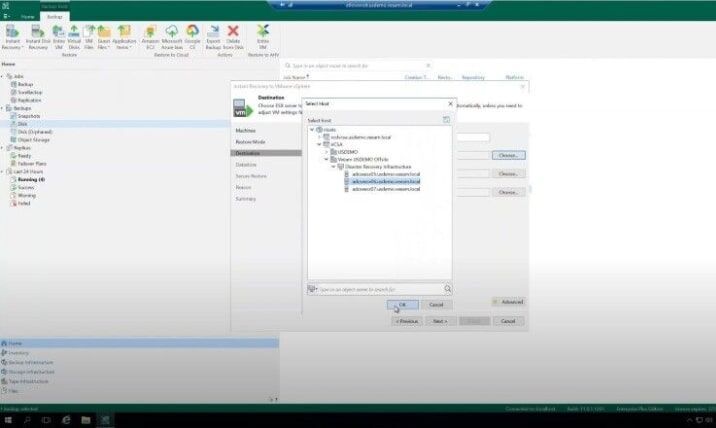
Demo #2
Detect and respond to Malware attacks
Identifying risks and acting fast are critical when it comes to overcoming a cyberattack. Veeam’s Malware Detection Engine empowers administrators to uncover threats at the time of backup. Powered by AI and machine learning, data is scanned for malware, signs of encryption, and a litany of other indicators. When coupled with the Veeam Incident API, third parties can alert Veeam Data Platform about threats found in production and trigger backups for affected machines.